
The Wall Using to create OAuth Provider
OpenID Connect. OpenID Connect (OIDC) is an authentication standard built on top of OAuth 2.0. It defines an ID token type to pair with OAuth 2.0 access and refresh tokens. OIDC also standardizes areas that OAuth 2.0 leaves up to choice, such as scopes, endpoint discovery, and the dynamic registration of clients.
How OAuth 2.0 Works
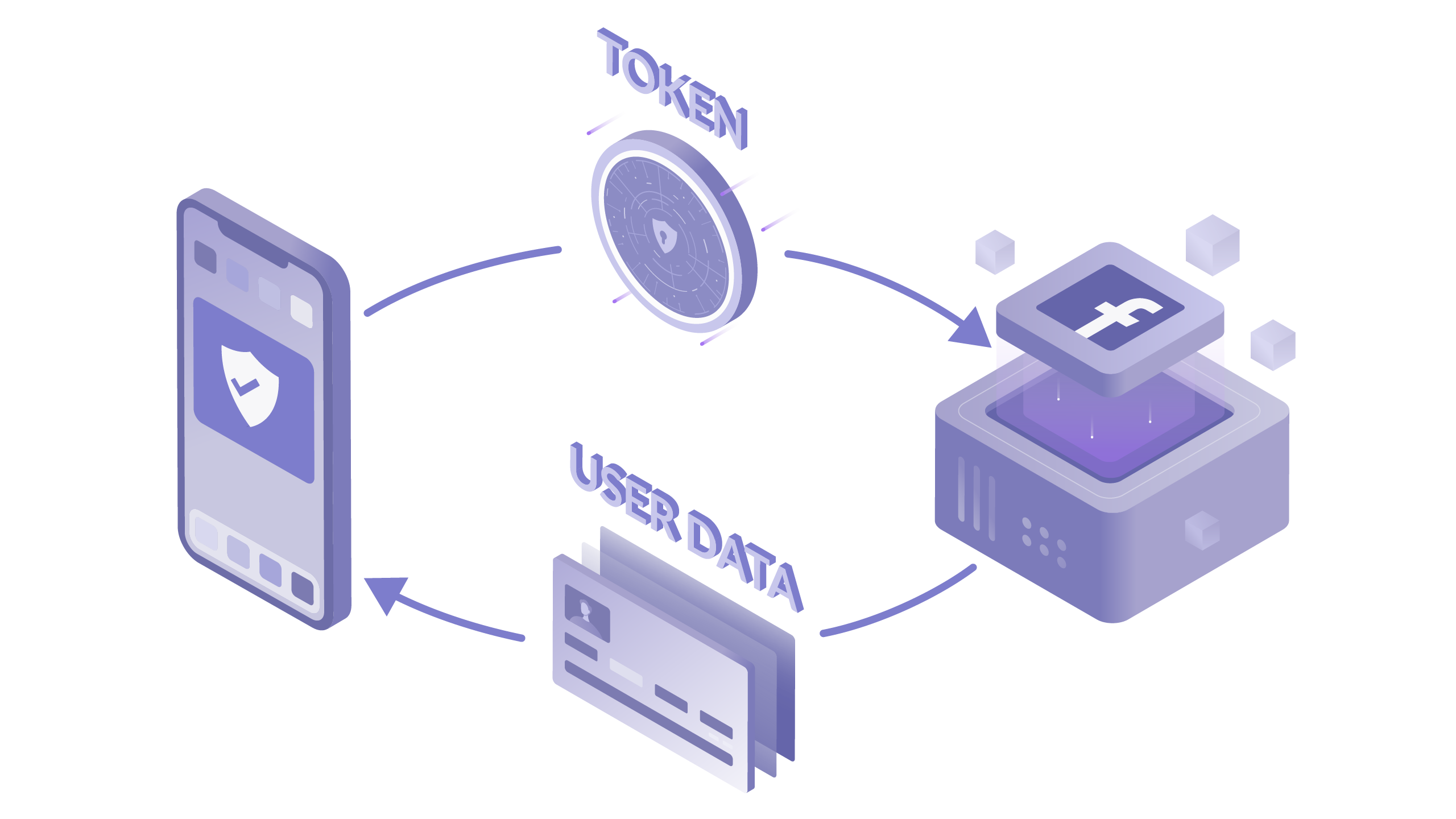
OAuth is implemented in numerous real-world scenarios to enable secure access to resources. Below are some examples, along with simplified pseudo-code snippets: 1. Social Media Login (e.g., Facebook Login): Many websites and apps allow users to log in or sign up using their social media accounts.
Microsoft Oauth Flaw Opens Azure Accounts To Takeover Flipboard
START YOUR ENGINES. Mecum Auctions will showcase a stunning collection of 4,000 vehicles at the Osceola Heritage Park in Kissimmee, FL on January 2-14, 2024.

Memahami alur kerja OAuth 2.0 YouTube
Judul: "Memahami alur kerja OAuth 2.0"***** 😊 *****Link Komunitas Kabayan Codinghttps://t.me/kabayan_coding***** 😊 *****Bagi yang ingin berkon.
Buy Introduction To Oauth With Node Js Twitter Api 1 2 A Simpler
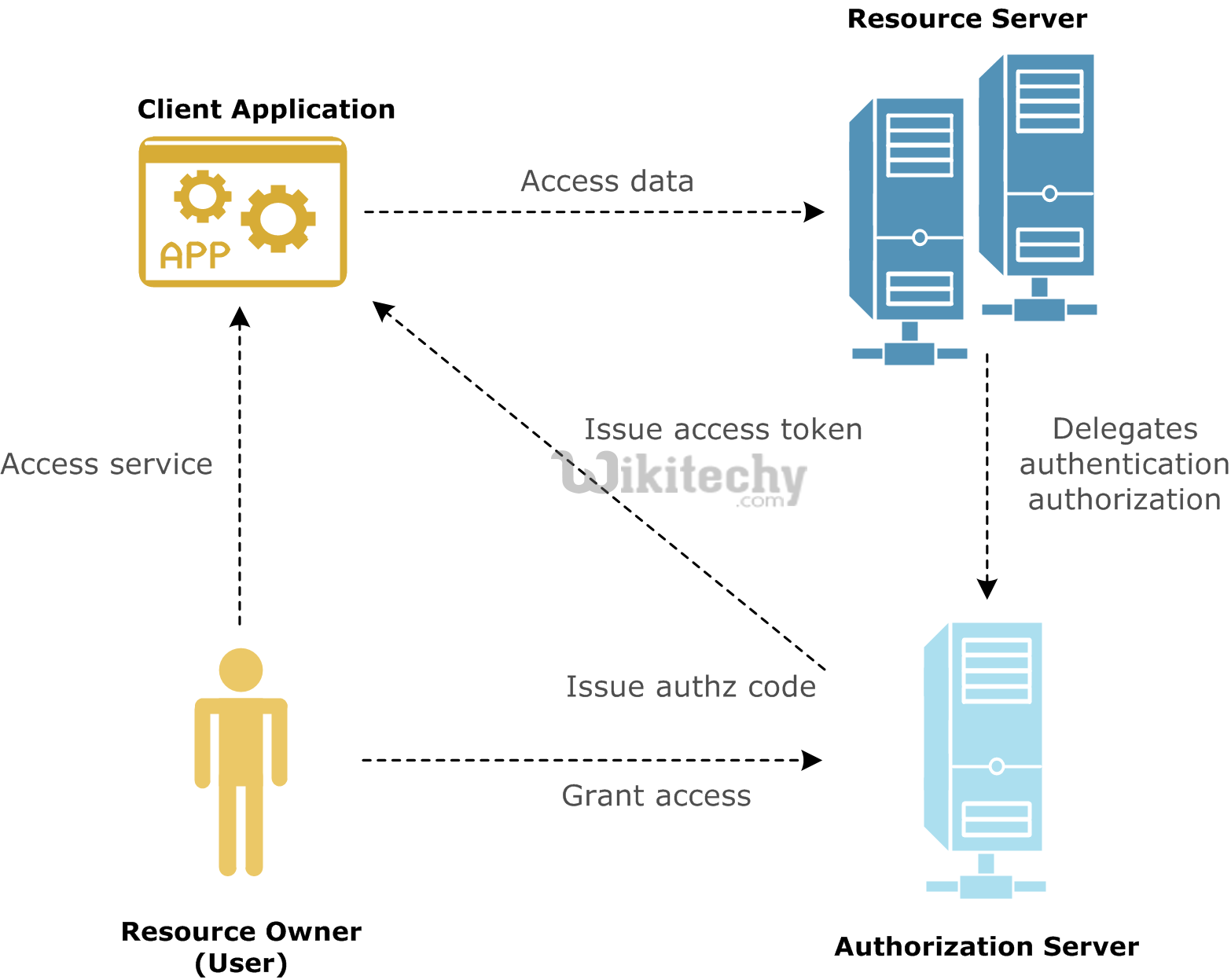
OAuth 2.0 is an authorization framework or protocol that lets an application get limited access to another service on behalf of a user. As part of the framework, a user explicitly grants the application access to their service account. By the way, OAuth 2.0 is an updated version of the older OAuth 1.0 protocol which should be considered obsolete.
What is OAuth and How it works?
Many apps today are actually a front-end for a series of API calls. APIs are necessary to proper functioning of such applications, but if you don't protect them, bad actors can exfiltrate data, DDoS your servers, or otherwise abuse them. OAuth is one of many solutions you can use to protect your APIs and other resources.

What is OAuth? (An Introduction to OAuth and OpenID) The Genius Blog
The OAuth 2.0 specification defines a delegation protocol that is useful for conveying authorization decisions across a network of web-enabled applications and APIs. OAuth is used in a wide variety of applications, including providing mechanisms for user authentication. This has led many developers and API providers to incorrectly conclude that.

What is OAuth 2 and how does it work? The Security Buddy
The explanation of the difference between OpenID, OAuth, OpenID Connect: OpenID is a protocol for authentication while OAuth is for authorization. Authentication is about making sure that the guy you are talking to is indeed who he claims to be. Authorization is about deciding what that guy should be allowed to do.

OAuth 2.0 An Overview and Simple Guide to build an Sample Application
Memahami Oauth2. OAuth2 merupakan perkembangan dari OAuth 1. Secara resmi, OAuth2 adalah versi yang sekarang aktif sehingga penyebutan OAuth saat ini juga mengacu ke OAuth2.. OAuth is an open protocol to allow secure authorization in a simple and standard method from the Web, mobile, and desktop application.

Memahami OAuth 2.0 (API Security) UNIKOM Codelabs Medium
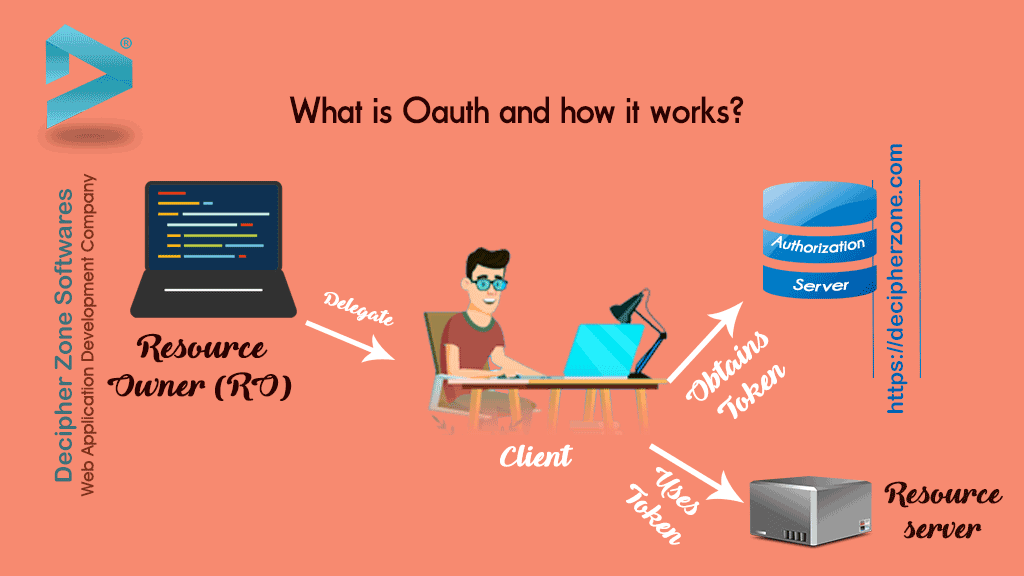
OAuth (Open Authorization) is an open standard for token -based authentication and authorization on the Internet.

CI4 Integrasi OAuth Simplifikasi Keamanan Autentikasi Pada Aplikasi
OAuth, which stands for Open Authorization, is an open standard authorization framework that enables users to share account information securely with third-party services such as Facebook and Google, without exposing their credentials. An intermediary, the access token, is provided to the third-party service which then authorizes specific user.

Memahami OAuth GoindoTI
OAuth 2 is an authorization framework that enables applications — such as Facebook, GitHub, and DigitalOcean — to obtain limited access to user accounts on an HTTP service. It works by delegating user authentication to the service that hosts a user account and authorizing third-party applications to access that user account.
OAuth for Mail Server Configuration
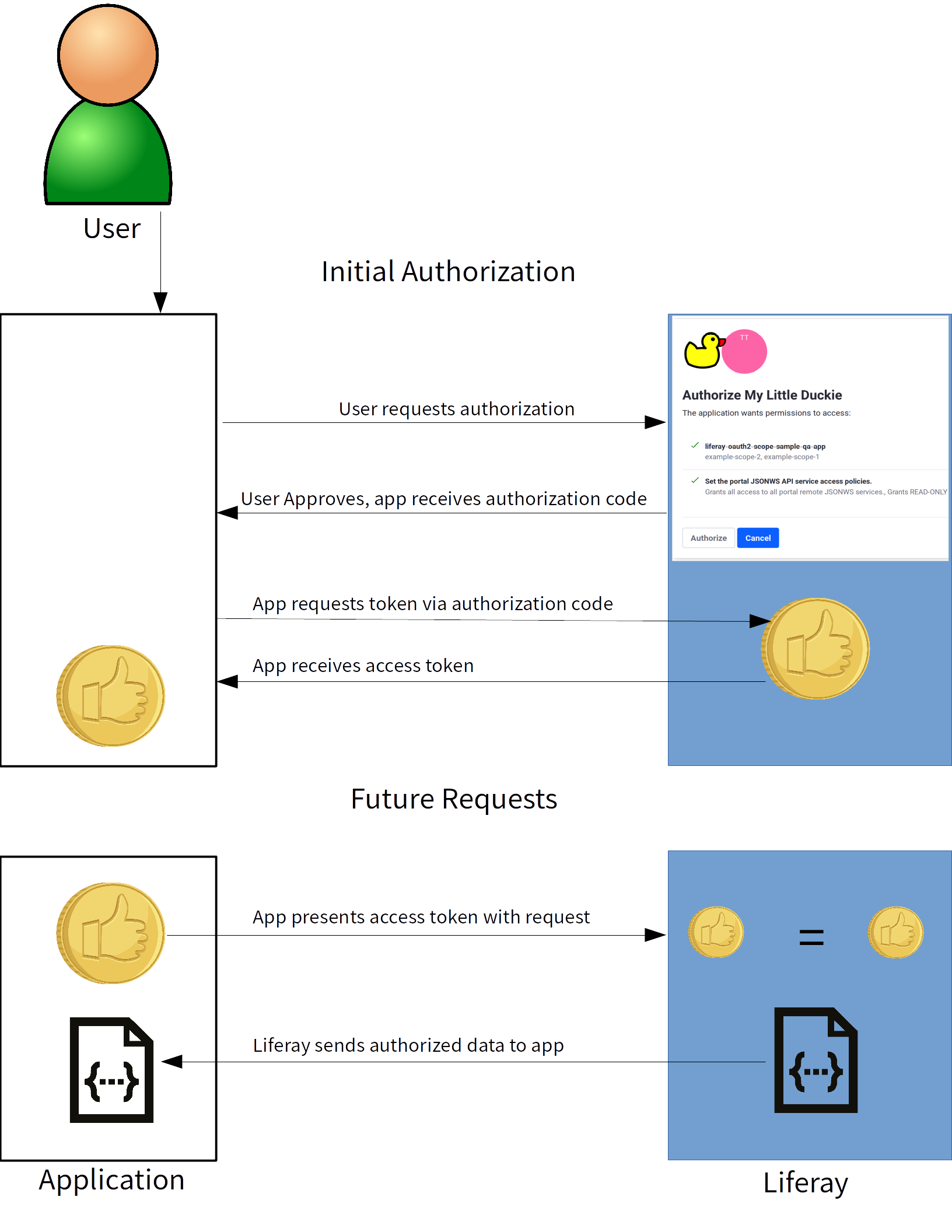
Ini adalah OAuth di level tinggi. Memahami protokol ini sangat penting bagi setiap insinyur perangkat lunak, pakar keamanan, dan bahkan peretas. TL; DR. Panduan lengkap untuk OAuth 2.0 dan OpenID Connect, dua protokol yang paling banyak digunakan di internet saat ini untuk otorisasi dan autentikasi. OAuth 2.0 digunakan untuk otorisasi dan.
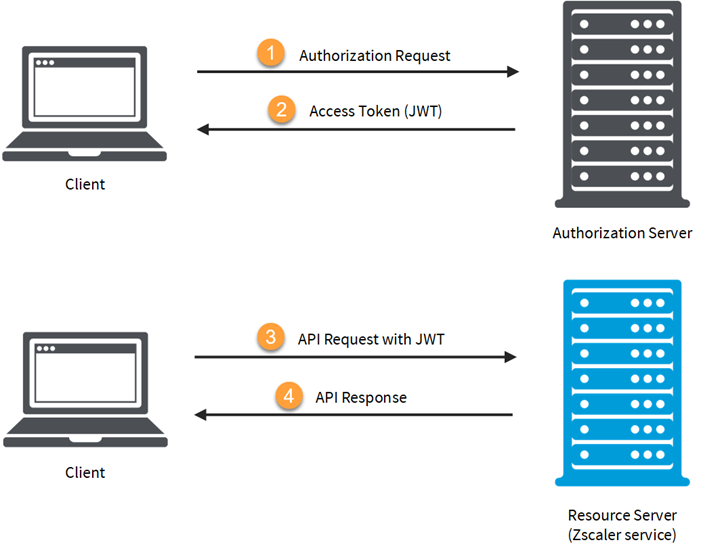
About API Authentication Using OAuth 2.0 Zscaler
1. Pengantar: Memahami OAuth dan Keamanan Aplikasi Web. Sudah menjadi rahasia umum bahwa keamanan adalah salah satu aspek krusial dalam pengembangan aplikasi web modern. Dengan semakin kompleksnya serangan siber dan tantangan keamanan, pengembang harus mencari cara yang efisien dan aman untuk mengelola autentikasi pengguna pada aplikasi mereka.

OAuth(Open Authorization) and its Use Cases with OAuth Flows by
OAuth server akan menjembatani interaksi antara Resource Owner (user) dan Client ( Third party apps ). OAuth Server yang akan melakukan proses Authentication dan Authorization. Client akan.

OAuth Authentication Onpipeline CRM Support
Ladies and Gentlemen, Introducing OAuth 2.0. OAuth 2.0 is a security standard where you give one application permission to access your data in another application. The steps to grant permission, or consent, are often referred to as authorization or even delegated authorization.You authorize one application to access your data, or use features in another application on your behalf, without.